DATA SKIMMING ATTACKS: HOW YOUR CREDIT CARD DATA GETS STOLEN FROM E-COMMERCE SITES
Data skimming attacks
As predicted, the move to EMV, or “chip,” security in payment cards has shifted criminals’ efforts away from card-present fraud–such as card skimming–and put the focus on e-commerce. Attackers will take a “shotgun” approach, compromising as many websites as possible at a time, hoping that some might turn out to be lucrative. All cybercriminals have to do is load malicious code into e-commerce shopping cart pages, disguise them well enough to be missed, and wait for the submissions to come in. In some cases, malicious code is disguised as a google tag or as a domain that sounds related to the website or payment processor. Symantec reported that on average, 4,800 unique websites are compromised with formjacking code each month. This ongoing, lucrative effort by cybercriminals targets providers of all sizes. Recent research by RiskIQ reported that such attacks by the “Magecart” group are actually much more widespread than initially believed.
Magecart attack
The term Magecart was coined years ago and is linked to the name of the group of criminals who first used this technique in attacks against e-commerce websites to steal payment card data. The name Magecart derives from the words “Magento” and “shopping cart.” The Magento CMS is one of the most common targets of the Magecart groups, as it provides checkout and shopping cart functionality for e-commerce websites. The attacks are attributed to an umbrella of financially motivated threat actors, each with its own characteristics, that compromise e-stores by injecting malicious code designed to steal visitors' credit card data while purchasing products on sale. This malicious code is also called data skimmer, software skimmers or e-skimmer. The name comes from physical skimmers, which are devices that criminals superimpose on ATM slots to steal bank customer card data. The first data skimming attacks were observed as early as 2010. In 2022 researchers identified more than 100,000 70,000 compromised stores world wide that contained a digital skimmer at one point in time. More than 200,000 stores were affected if you include supply chain attack victims. But data skimming is not limited to Magento, other open source ecommerce platforms are also targeted by cybercriminals.
Over time, these attacks have become more stealthy, and attackers have developed systems to automate their attack chain. Some groups use tools that can scan the web for outdated e-commerce sites or that use vulnerable plugin-ins and then automatically inject malicious software. Stolen credit cards are then sold by cybercrime organizations on the dark web for $3 to $45 each. Data skimming attacks expose financial and personal data, can damage brand reputation and consumer trust, and could result in fines due to non-compliance with privacy regulations. This criminal practice has allowed cybercriminal gangs to compromise several tens of thousands of e-commerce sites, including those of well-known brands.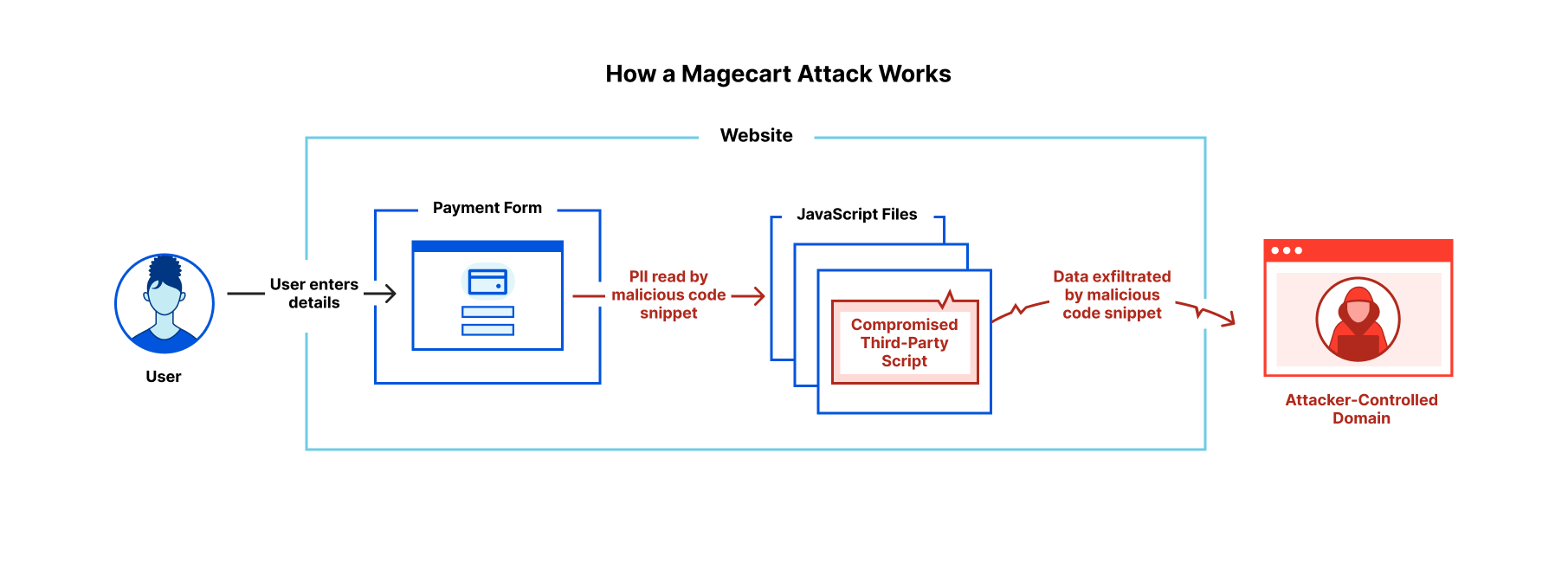
British Airways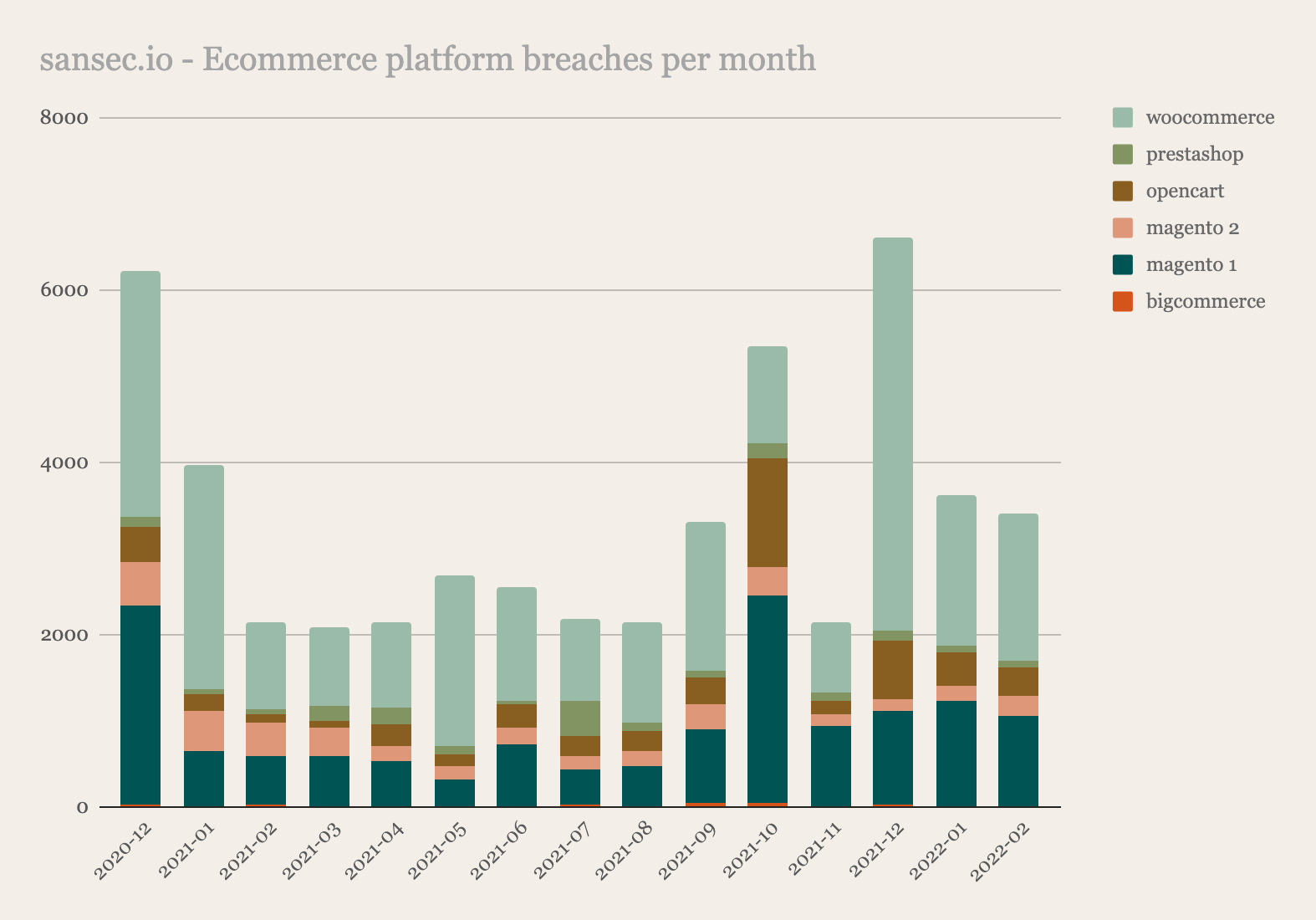
In September 2018, British Airways suffered a data breach that exposed the personal information of 400,000 customers. The hackers potentially accessed the personal data of approximately 429,612 customers and staff. Exposed data included names, addresses, payment card numbers, and CVV numbers of 244,000 BA customers. Experts believe the hackers also accessed the combined card and CVV numbers of 77,000 customers and card numbers only for 108,000 customers. An investigation conducted by researchers at RiskIQ revealed that the attack on the airline was carried out by the notorious crime gang MageCart. An interesting aspect of many data skimming attacks is that the threat actors maintain persistence. According to a report published by the security firm Imperva, one out of five eCommerce websites that were previously compromised by Magecart are re-infected in a matter of days. The attackers gain persistence by establishing multiple backdoors and creating rogue admin accounts. Other reinfection mechanisms adopted by Magecart groups, include the setup of hidden periodic tasks and database triggers, which re-install the malicious code in case it was removed by the admins. The attackers use to obfuscate the e-skimmer code to avoid detection. In some cases, the skimmer employed in the attacks was designed to check for the use of virtual machines for the same reason. Cybersecurity firms have spotted hundreds of different software skimmers over time, and threat actors are adopting multiple technique to avoid detection and bypass security measured implemented by merchants to protect their infrastructure.
Using a PCI compliant payment service? Your buyers’ credit card information could still be stolen.
PCI compliant payment services hosted within an iframe are not immune from Magecart attacks. Website owners are still responsible for any stolen personally identifiable information (PII) or resulting fines. The HUMAN Satori Threat Intelligence and Research team has uncovered a novel technique for bypassing hosted fields iframe protection, which enables Magecart attackers to skim credit card data while allowing successful payment transactions. This stealthy attack technique gives no indication of compromise to the user or the website admin, enabling the skimming to persist on checkout pages for a long time. The users don’t suspect any malicious activity since the transaction succeeds as expected.
How can DEKENEAS Browser Attack Detector identify data skimming attacks
As cybercriminals must hide and obfuscated their malicious implants, these implants fit all the features of web malware that our artificial intelligence (AI) algorithms are trained to detect. Even though currently these client-side data skimming attacks are detected as-is, having already successfully detected a plethora of data skimming implants, at this moment these implants are marked as "high risk" but are only considered suspicious, with no confirmed specific "data skimming" infection. However we are currently upgrading our artificial intelligence (AI) assisted detection to specifically detect data skimming attacks.

CONTACT US
office@dekeneas.com @dekeneas @dekeneas
FREQUENTLY ASKED QUESTIONS
Q: Who is at risk of getting attacked through browser exploits?
A: Considering that browsers are part of our day to day activities, being for work or pleasure, anyone can be targeted with a browser exploit. However, if you work in a sensitive environment, and your job requires you to have access to sensitive organizational resources, the risk of being attacked with a browser exploit increases significantly. But browser exploits are not the only browser attacks..
Q: How could a browser exploit affect my work place?
A: Organizational network defenses have become increasingly performant in the past years, with organizations investing allocating increased budgets to cybersecurity, therefore making it harder for attackers to directly attack organization's network perimeter. But at the same time, organizations tend to not address the insider threat with the same type of resilience. Therefore if you use your smartphone, laptop or tablet to access organizational resources attackers gain a foothold inside the network.
Q: What other browser attacks are outhere, except device compromises through exploits?
A: While browser exploits are the most dangerous type of browser attack, there are also cryptojacking attacks and data skimming attacks. Cryptojacking attacks use your device to mine for cryptocurrencies consuming your CPU cycles for the benefit of the attackers. Data skimming attacks are usually placed in online shops or other type of websites which require the user to enter banking or credit card informations. They are totally invisible to the end user and any security product he may use and they collect these informations to be sent to the attackers. Cyber criminal groups such as Magecart are getting the spotlight in the past years but these types of attacks have been going for at least a decade and they continue to affect hundreds of thousands of websites around the world.
Q: My antivirus is updated to the latest. Am I still vulnerable?
A: Unfortunately yes. Antivirus products use signatures to detect attacks. If a signatures has not been previously generated, the attack goes unnoticed to the antivirus product.
Q: I have the latest next-generation detection and response endpoint protection. Am I still vulnerable?
A: Unfortunately yes. Even the most performant XDR endpoint protection uses some type of signature scanning corroborated with behavioral analysis and even artificial intelligence (AI). However, they cannot be installed on smart phones, tablets or IoT devices. And even for traditional systems, such as desktops or laptops they fail to accurately identify attacks, mostly because browsers are very difficult to inspect and instrument and because these attacks are specifically crafted to look like normal user activities.
Q: I only browse behind my corporate network. Am I still vulnerable?
A: Unfortunately yes. Network defense systems are unable to properly inspect HTTP/S traffic, even if they are able to decrypt the encrypted communication. Dynamic HTML code, such as Javascript, makes it impossible to an intermediate product to know how the final code will be rendered inside user's browser, therefore they are unable to guess wether an attack is happening or not. This is how big banks and corporations have been compromised in the past.
Q: I use a different web malware scanner. Isn't that enough?
A: Unfortunately no. All the commercially available web malware scanners use signature scanning to detect attacks against browsers. While this approach is sufficient to detect known attacks, they have no way of detecting unknown attacks. Most web malware today is crafted in such way that it looks different for every infection, even inside the same website. Also, most of the commercially available web malware scanners only scan the first page of the website, while in reality the attack can be hidden deeper inside the website.
Q: Ok, and how does DEKENEAS does it then?
A: We have an artificial intelligence (AI) algorithm trained to recognize features that might serve a malicious purpose. And we do not consider these features separately, our AI tries to understand how these features could be used in conjunction to serve a malicious purpose. This approach allows us to select only those HTML elements, such as scripts or iframes, that have a high risk of being used for malicious purposes. After this filtering, we launch each suspicious element inside a dynamic analysis environment which mimicks in the slightiest detail the behaviour of a legitimate user, in order to bypass any anti analysis or instrumentation environment detection techniques the malware might use. We record these interactions and also we record all the traffic exchanged between our dynamic analysis environment and the suspicious HTML element. The recorded traffic is analyzed by another AI algorithm in order to determine wether there are any signs of attacks inside the traffic. If there were no interactions during the dynamic analysis and there were no signs of attack inside the network traffic recorded, we still consider the element suspicious, needing manual analysis by one of our specialists.
Q: So every suspicious script is possibly an attack?
A: Sometimes, yes. Some other times, no. There could be an attack that evaded our dynamic analysis environment, and it needs further inspection, but also, sometimes, not very often, legitimate HTML elements use the same techniques as malware and we detect that. But it's better to be safe than sorry.
Q: I started my scan a few hours ago and it still did not finish. Is there something wrong?
A: Normal websites have thousands of pages, each of these pages containing tenths or hundreds of HTML elements that need to be analyzed. Even though our AI is doing a fantastic job at eliminating benign looking elements, there are still tenths or hundreds of these elements that need to be passed to our dynamic analysis environment. This is the most consuming part of the process, as we try to mimick in the slightiest detail the behavior of a normal user. So, especially at the first iteration, a scan could last for a few hours, depending on the number of suspicious HTML elements found.
DEKENEAS
DEKENEAS is a unique product, being the only publicly available tool able to identify with great accuracy both known and unknown browser exploits ("0day") and attacks by the means of artificial intelligence algorithms, instead of traditional signature scanning. Our approach is mainly focused on detection of unknown attack vectors for the vast majority of existing desktop browsers, such as Chrome, Edge, Firefox or Safari, but also mobile devices browsers for Android and iPhone. Our artificial intelligence algorithms understand the code of the website before actually executing it, and tries to understand if the code constructs encountered are malware specific or they are benign. Also it tries to figure out if there are special conditions for certain code to run, such as specific User-Agent strings, language settings or IP addresses. All this information is later used during the instrumentation performed by Dekeneas Sandbox, which comes as a double check, actually executing the suspicious code in a real environment according to the special conditions requested by the analyzed code, launching a specific browser with specific language or country settings in a specific environment (desktop or mobile), and analyzing how the code interacts with the browser. In addition to code instrumentation Dekeneas Sandbox also analyzes the traffic generated looking for exploitation gadgets, therefore maximizing the chances of identifying unknown attacks.
- Signature less scanning - browser malware looks different from infection to infection so signature scanning is mostly useless
- In-depth scanning of websites - most attacks are not placed in the first page
- Code interpretation without actually executing the code - greatly optimizing analysis time
- Detection of attacks in the early stage - as opposed to traditional methods who detect post-exploitation stage of infection
- Anti anti analysis capabilities - most browser attacks are highly obfuscated and have anti analysis capabilities
- Anti evasion capabilities - most browser attacks are able to evade detection by targetting specific browsers, technologies or settings
Dekeneas On-Premise WSG
The Dekeneas WSG range is a family of secure web gateway appliances, integrating the advanced artificial intelligence malware scanning capabilities of the DEKENEAS into your network, protecting your users from some of the most elusive attacks used by hackers.
WSG-010
Virtual Appliance
- Administration interface
- Transparent Proxy (network traffic redirector, WCCP redirect)
- Explicit Proxy (supports PAC installation, WPAD server, Active Directory)
- HTTP/S inspection
- URL filtering based on DEKENEAS
- Integrated DEKENEAS engine
- Supports both IPv4 and IPv6 protocol stacks
- Supports integrations with external threat intelligence feeds, commercial or open source
- Custom and automated whitelisting of websites
- Custom and automated blacklisting of malicious websites
- Automated antivirus scanning of files in transit
- Automated updates of AV signature database
- Automated blocking of malicious files in transit
WSG-100
Hardware Appliance

- Administration interface
- Transparent Proxy (network traffic redirector, WCCP redirect)
- Explicit Proxy (supports PAC installation, WPAD server, Active Directory)
- HTTP/S inspection
- URL filtering based on DEKENEAS
- Active Directory integration (multi realm, multi forest NTLM, single sign on through browser stored credentials)
- Inline sandbox
- Bandwidth management
- Integrated DEKENEAS engine
- Supports both IPv4 and IPv6 protocol stacks
- Supports integrations with external threat intelligence feeds, commercial or open source
- Custom and automated whitelisting of websites
- Custom and automated blacklisting of malicious websites
- Automated antivirus scanning of files in transit
- Automated updates of AV signature database
- Automated blocking of malicious files in transit
- Automated YARA scanning of files in transit
- Automated updates of AV signature database
- Automated blocking of malicious files in transit
- Data leakage prevention through artificial intelligence classification
WSG-200
Hardware Appliance

- High availability setup
- Administration interface
- Transparent Proxy (network traffic redirector, WCCP redirect)
- Explicit Proxy (supports PAC installation, WPAD server, Active Directory)
- HTTP/S inspection
- URL filtering based on DEKENEAS
- Active Directory integration (multi realm, multi forest NTLM, single sign on through browser stored credentials)
- Inline sandbox
- Bandwidth management
- Integrated DEKENEAS engine
- Supports both IPv4 and IPv6 protocol stacks
- Supports integrations with external threat intelligence feeds, commercial or open source
- Custom and automated whitelisting of websites
- Custom and automated blacklisting of malicious websites
- Automated antivirus scanning of files in transit
- Automated updates of AV signature database
- Automated blocking of malicious files in transit
- Automated YARA scanning of files in transit
- Automated updates of AV signature database
- Automated blocking of malicious files in transit
- Data leakage prevention through artificial intelligence classification
